Today digital era is a boon if we are using it in the correct manner. On the other hand, the devil’s mind is always present to steal your personal digital data. To prevent data breaches, Encryption is being used in secure systems. Encryption is a method to secure data that converts a readable data format into an encoded format that can only be read after it has been decrypted correctly. Technically, Encryption is a common process in cryptography that encodes a message or information so that only authorized individuals or entities can access it.
History and working of Encryption:
Encryption is a general process to prevent access to data from unauthorized persons. This technique is historical even before the computer era. For example, Ancient Spartans (The Spartan army was the principal ground force of Sparta) used an early transposition cipher (a technique to hide data) to scramble the order of the letters in their military communications. The process works by writing a message on a piece of leather wrapped around a hexagonal staff of wood known as a scytale. When the leather strip is wound around a correctly sized scytale, the letters line up to form a correctly synchronized message; on the other hand, when the strip is unwound or wrapped around other scytale the message becomes unreadable.
Encryption converts a human-readable plain text into a Delphic text, known as cipher text. This cipher text is generated by using cryptographic mathematical models. To recover plain text from cipher text is known as decryption.
As an integral part of security, encryption protects data from theft, manipulation, or being compromised. It works by mixing up data into a secret code or encryption key that only key can unlock or filter out the data.
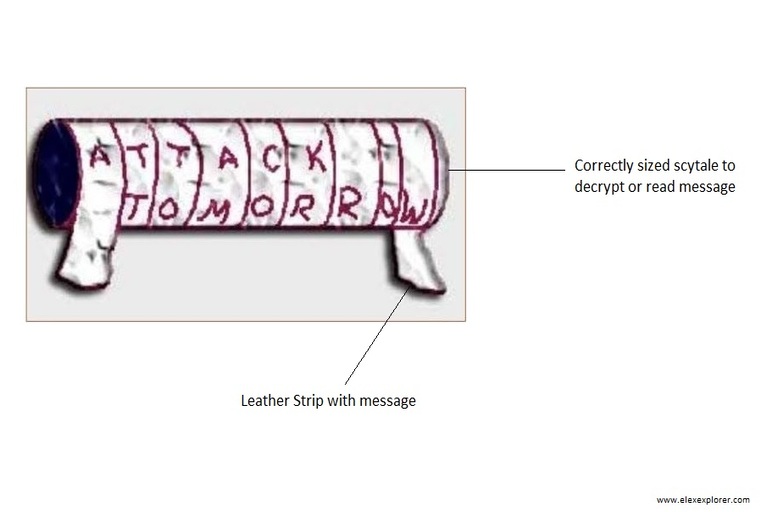
Old Encryption technique
Types of Encryption:
There are two common types of encryption: symmetric and asymmetric.
Symmetric encryption:
Symmetric encryption is a common and simple type that includes the same key for encryption and decryption. This means that the sender and receiver must use the same key to encrypt and decrypt the data respectively. Symmetric encryption is faster and more efficient than other ones. Because of that, it is getting preferred for bulk data transfer. Some common symmetric encryption methods are Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple Data Encryption Standard (3DES).
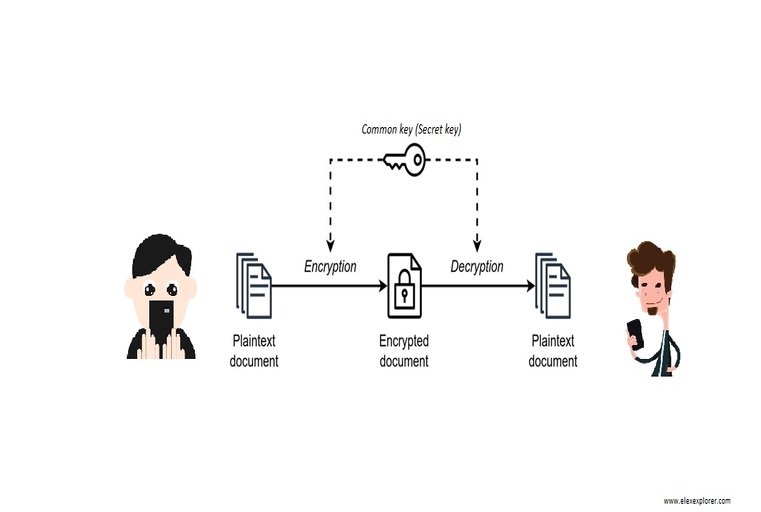
Symmetric Encryption
Asymmetric encryption:
Asymmetric encryption is also known as public-key cryptography. This encryption technique uses two separate keys. Here sender and receiver have their own private and public keys. Public keys are used to encrypt the data whereas private keys are used to decrypt the data. The owner of data keeps the private key secret whereas the public key is available to the public. Data that are encrypted using the recipient’s public key can only be decrypted with the corresponding private key. Asymmetric encryption is slower and more complex but most importantly it is very secure. It eliminates the need for a secure key exchange that is required in a symmetric encryption process. Common asymmetric encryption methods include RSA and ECC algorithms.
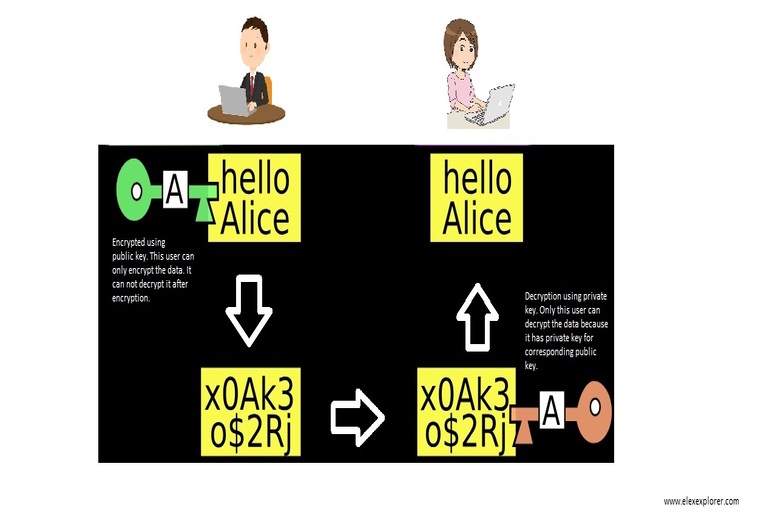
Asymmetric Encryption
Merits and Demerits of Encryption:
Encryption has several merits for an individual as well as organizations, including:
- Compliance: Encryption can help organizations to meet legal and regulatory requirements for data protection. Some organizations like health care and finance need strict data protection and encryption helps them to achieve their standards and ensure compliance.
- Data Integrity: Encryption can prevent data from being tempered and maintain its integrity.
- Enhances security: Encryption provides an additional level of security to protect against data breaches, cyber-attacks, and other cyber threats.
- Boosting consumer trust: For a consumer-based organization, it is a boon. Encryption boosted trust and confidence in an organization by publicly disclosing the use of encryption technologies for their services. For example; Visa, a payment company, uses encryption to secure the payment of their consumers. Due to this consumers have confidence and trust over the visa for their services.
Every coin has two sides. Encryption also has some disadvantages to consider. The demerits of encryption include:
- Cost: Encryption can be expensive because it needs some additional resources, implantation process, and upgrades to perform operations.
- Compatibility: Encryption technique can become a cumbersome process when dealing with different systems and applications. It can be challenging to ensure that all authorized users can read or access encrypted data correctly.
- Performance impact: The encryption process can slow down the performance of an application or system because it needs additional time for processing and generating desired outcomes.
- Data lost: If the user forgot or lost the encryption key then the data become inaccessible.
Importance of Encryption:
Encryption plays a crucial role in cyber security and data protection, as it protects personal and confidential information and enhances the security of one-way or two-way communication between two entities. As a vital element of data security, encryption makes it nearly impossible to breach or steal data since only those with an encryption key can access the data information correctly.
Thanks for reading. See you soon with another exploration!